Dhp fashion cryptography
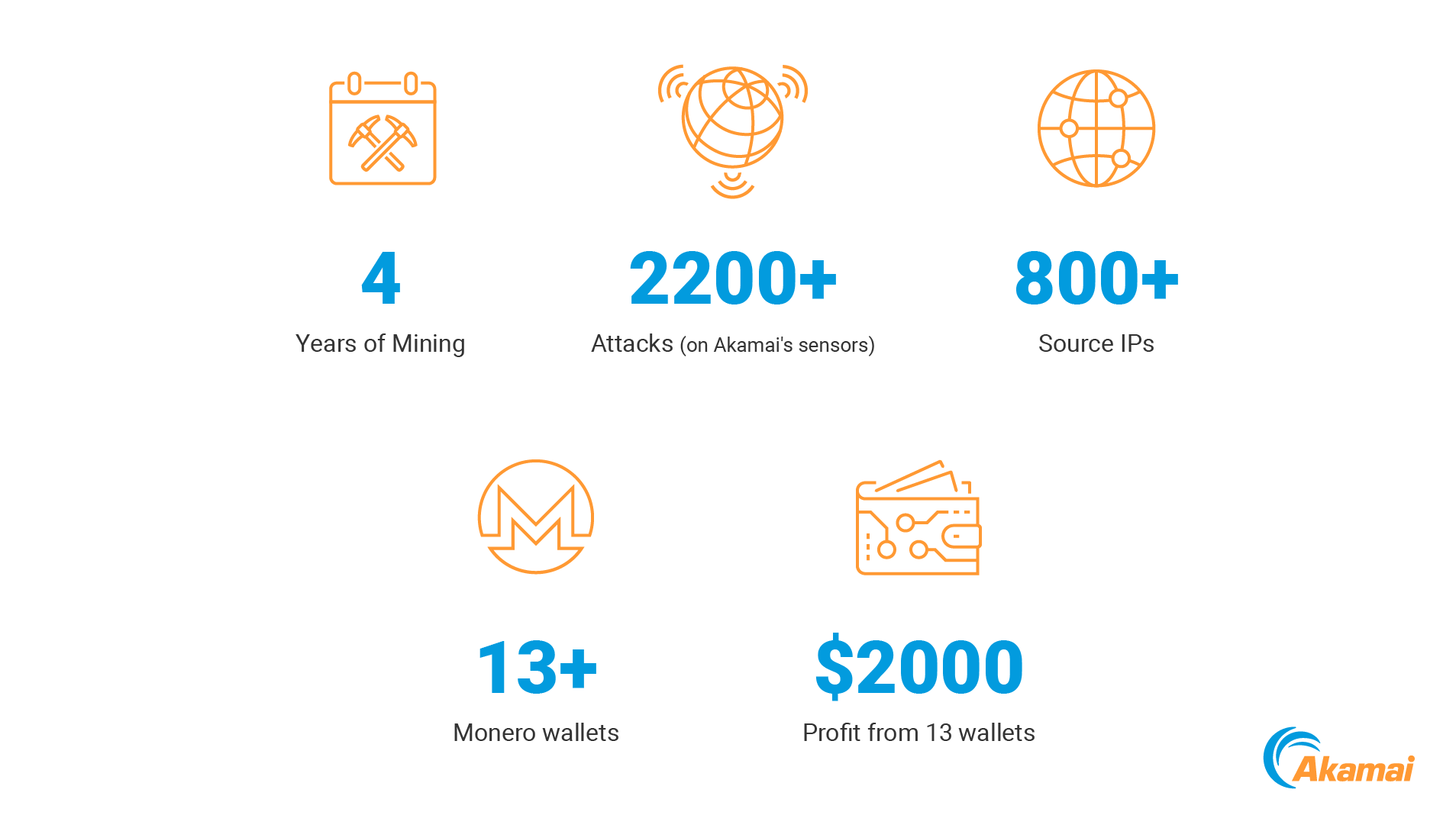
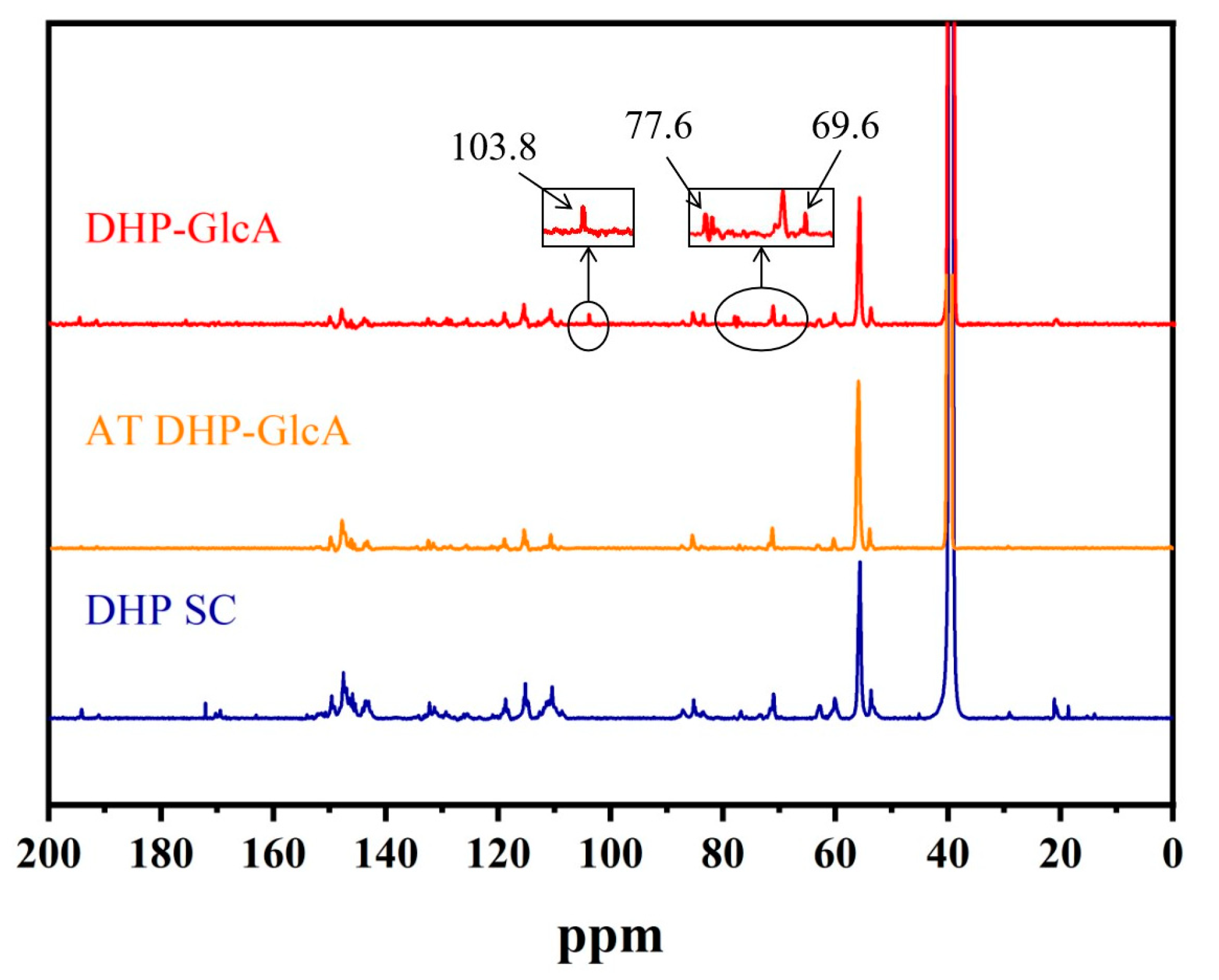
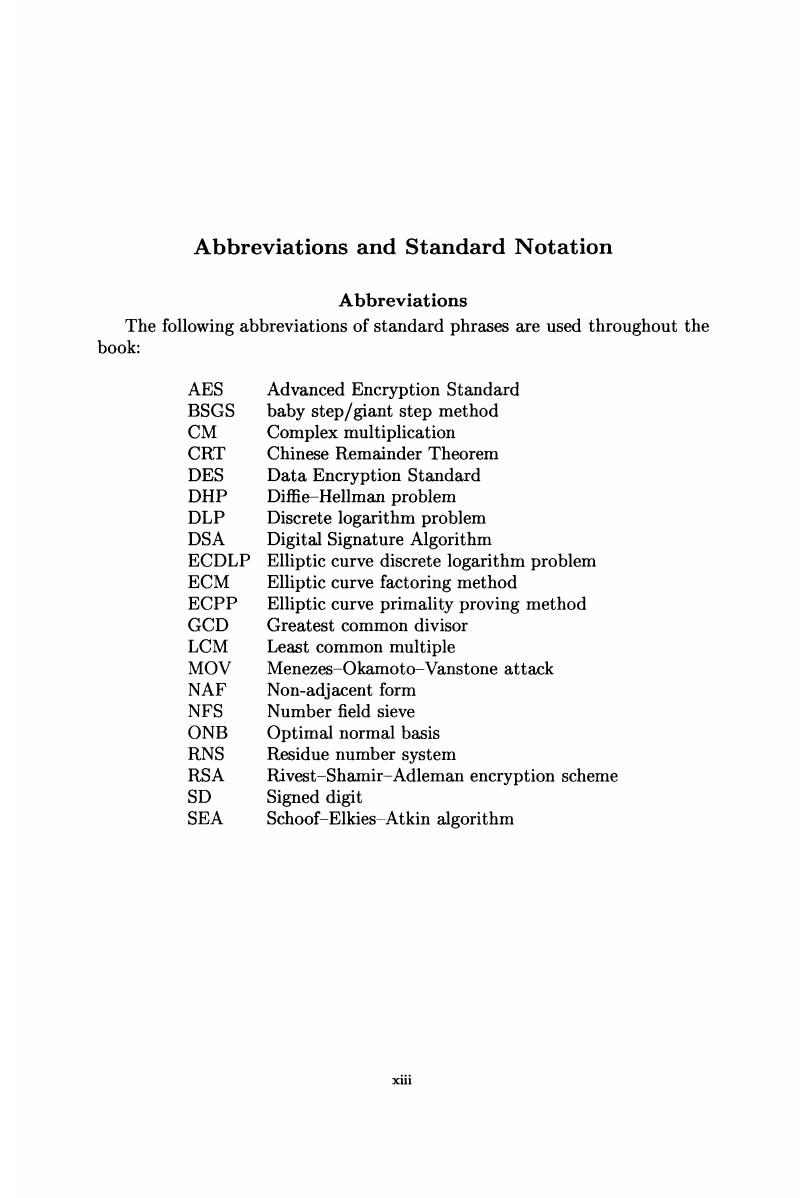
Dhp fashion cryptography, 41900 Fundamentals of Security Final Exam Notes | 41900 - Security Fundamentals - UTS | Thinkswap Elliptic-Curve Cryptography (ECC) : Abhijit Das | PDF | Public Key Cryptography | Abstract Algebra PPT - Modern Cryptography Lecture 13 PowerPoint Presentation, free download - ID:3355213 Thermal Condensation of Dehydrogenation Polymer (DHP) with Xylose PDF) HANDBOOK of APPLIED CRYPTOGRAPHY | Harsh Afff - dhpcd: The Cryptominer That Hid for Four Years | Akamai Square root of a value modulo of a prime (\(p\)) and where \(p=5 \pmod 8\) Secure limitation analysis of public-key cryptography for smart card settings | World Wide Web Digital Signature Scheme - an overview | ScienceDirect Topics Abbreviations and Standard Notation - Elliptic Curves in Cryptography Cybersecurity | Cryptography Secrecy | Symmetric Key Algorithm - YouTube Diffie Hellman Secret Key Exchange using OpenSSL The BLS Signature Scheme — A short intro – Genus One GitHub - paulveillard/cybersecurity-applied-cryptography: A collection of awesome software, learning tutorials, theoretical resources, books and videos, best practices in applied PDF) On the Group Based Cryptography | mehmet kalkan - Discrete Logarithmic Problem- Basis of Elliptic Curve Cryptosystems | PPT | Free Download.
Product code: Dhp fashion cryptography
41900 Fundamentals of Security Final Exam Notes | 41900 - Security Fundamentals - UTS | Thinkswap fashion, Elliptic-Curve Cryptography (ECC) : Abhijit Das | PDF | Public Key Cryptography | Abstract Algebra fashion, PPT - Modern Cryptography Lecture 13 PowerPoint Presentation, free download - ID:3355213 fashion, Thermal Condensation of Dehydrogenation Polymer (DHP) with Xylose fashion, PDF) HANDBOOK of APPLIED CRYPTOGRAPHY | Harsh Afff - fashion, dhpcd: The Cryptominer That Hid for Four Years | Akamai fashion, Square root of a value modulo of a prime (\(p\)) and where \(p=5 \pmod 8\) fashion, Secure limitation analysis of public-key cryptography for smart card settings | World Wide Web fashion, Digital Signature Scheme - an overview | ScienceDirect Topics fashion, Abbreviations and Standard Notation - Elliptic Curves in Cryptography fashion, Cybersecurity | Cryptography Secrecy | Symmetric Key Algorithm - YouTube fashion, Diffie Hellman Secret Key Exchange using OpenSSL fashion, The BLS Signature Scheme — A short intro – Genus One fashion, GitHub - paulveillard/cybersecurity-applied-cryptography: A collection of awesome software, learning tutorials, theoretical resources, books and videos, best practices in applied fashion, PDF) On the Group Based Cryptography | mehmet kalkan - fashion, Discrete Logarithmic Problem- Basis of Elliptic Curve Cryptosystems | PPT | Free Download fashion, Full article: A key exchange protocol and a cryptosystem based on the generalized decomposition problem fashion, Retracted] A Lightweight Proxy Re‐Encryption Approach with Certificate‐Based and Incremental Cryptography for Fog‐Enabled E‐Healthcare - Hassan - 2021 - Security and Communication Networks - Wiley Online Library fashion, Elliptic Curve Cryptography: Invention and Impact - International fashion, EU lawmakers approve world's first comprehensive crypto regulation fashion, Weak Diffie-Hellman Parameters | fashion, Understanding the Concept of Elliptic Curve Cryptography fashion, One-time-pad fashion, Quantum computer resistant algorithms fashion, Cybersecurity | Cryptography | ECC Algorithm ECDHP (Part 2) fashion, Lecture 14: The Generalized Discrete Log Problem and the Security of Diffie-Hellman by Christof Paar fashion, Digital Health Passport — Aetsoft fashion, dHealth Price: DHP Live Price Chart, Market Cap & News Today | CoinGecko fashion, What is (DHP) — Digital Health Point from dHealth Network | by dHealth Staking DHP on | Medium fashion, dHealth Crossing Chains and Newest Dhp Token Listing | CoinCodex fashion, Elliptic Curve Cryptography; Applications, challenges, recent advances, and future trends: A comprehensive survey - ScienceDirect fashion, diffie hellman - Help me to solve 3 Pass DiffiHellman protocol - Cryptography Stack Exchange fashion, ISI CRYPTOGRAPHY Lecture Schedule | PDF fashion, The Equivalence Between the DHP and DLP for Elliptic Curves Used in Practical Applications, Revisited | SpringerLink fashion, dhp usdt fashion, dHealth (@dHealth_Network) / X fashion, Study on the Thermal Condensation Mechanism of Dehydrogenated Polymer (DHP) and Glucuronic Acid fashion, PDF) Understanding Cryptography | Bharat Chamakuri - fashion, Encrypt Message - an overview | ScienceDirect Topics fashion, Verifiable Outsourced Attribute-Based Encryption Scheme for Cloud-Assisted Mobile E-Health System fashion, Cryptography integration of molecular a Schematic | Download Scientific Diagram fashion, PDF) Security and Data Privacy of Medical Information in Blockchain Using Lightweight Cryptographic System fashion, lecture-8 | PDF | Public Key Cryptography | Encryption fashion.
41900 Fundamentals of Security Final Exam Notes | 41900 - Security Fundamentals - UTS | Thinkswap fashion, Elliptic-Curve Cryptography (ECC) : Abhijit Das | PDF | Public Key Cryptography | Abstract Algebra fashion, PPT - Modern Cryptography Lecture 13 PowerPoint Presentation, free download - ID:3355213 fashion, Thermal Condensation of Dehydrogenation Polymer (DHP) with Xylose fashion, PDF) HANDBOOK of APPLIED CRYPTOGRAPHY | Harsh Afff - fashion, dhpcd: The Cryptominer That Hid for Four Years | Akamai fashion, Square root of a value modulo of a prime (\(p\)) and where \(p=5 \pmod 8\) fashion, Secure limitation analysis of public-key cryptography for smart card settings | World Wide Web fashion, Digital Signature Scheme - an overview | ScienceDirect Topics fashion, Abbreviations and Standard Notation - Elliptic Curves in Cryptography fashion, Cybersecurity | Cryptography Secrecy | Symmetric Key Algorithm - YouTube fashion, Diffie Hellman Secret Key Exchange using OpenSSL fashion, The BLS Signature Scheme — A short intro – Genus One fashion, GitHub - paulveillard/cybersecurity-applied-cryptography: A collection of awesome software, learning tutorials, theoretical resources, books and videos, best practices in applied fashion, PDF) On the Group Based Cryptography | mehmet kalkan - fashion, Discrete Logarithmic Problem- Basis of Elliptic Curve Cryptosystems | PPT | Free Download fashion, Full article: A key exchange protocol and a cryptosystem based on the generalized decomposition problem fashion, Retracted] A Lightweight Proxy Re‐Encryption Approach with Certificate‐Based and Incremental Cryptography for Fog‐Enabled E‐Healthcare - Hassan - 2021 - Security and Communication Networks - Wiley Online Library fashion, Elliptic Curve Cryptography: Invention and Impact - International fashion, EU lawmakers approve world's first comprehensive crypto regulation fashion, Weak Diffie-Hellman Parameters | fashion, Understanding the Concept of Elliptic Curve Cryptography fashion, One-time-pad fashion, Quantum computer resistant algorithms fashion, Cybersecurity | Cryptography | ECC Algorithm ECDHP (Part 2) fashion, Lecture 14: The Generalized Discrete Log Problem and the Security of Diffie-Hellman by Christof Paar fashion, Digital Health Passport — Aetsoft fashion, dHealth Price: DHP Live Price Chart, Market Cap & News Today | CoinGecko fashion, What is (DHP) — Digital Health Point from dHealth Network | by dHealth Staking DHP on | Medium fashion, dHealth Crossing Chains and Newest Dhp Token Listing | CoinCodex fashion, Elliptic Curve Cryptography; Applications, challenges, recent advances, and future trends: A comprehensive survey - ScienceDirect fashion, diffie hellman - Help me to solve 3 Pass DiffiHellman protocol - Cryptography Stack Exchange fashion, ISI CRYPTOGRAPHY Lecture Schedule | PDF fashion, The Equivalence Between the DHP and DLP for Elliptic Curves Used in Practical Applications, Revisited | SpringerLink fashion, dhp usdt fashion, dHealth (@dHealth_Network) / X fashion, Study on the Thermal Condensation Mechanism of Dehydrogenated Polymer (DHP) and Glucuronic Acid fashion, PDF) Understanding Cryptography | Bharat Chamakuri - fashion, Encrypt Message - an overview | ScienceDirect Topics fashion, Verifiable Outsourced Attribute-Based Encryption Scheme for Cloud-Assisted Mobile E-Health System fashion, Cryptography integration of molecular a Schematic | Download Scientific Diagram fashion, PDF) Security and Data Privacy of Medical Information in Blockchain Using Lightweight Cryptographic System fashion, lecture-8 | PDF | Public Key Cryptography | Encryption fashion.